Basic Access Authentication and a more secure variant named Digest Access Authentication, are described in RFC 2617, which discusses the security issues with both, including MITM (Man In The Middle) attacks.
Secure Basic authentication combines the simplicity of Basic authentication with the security provided by public-key cryptography. Simplicity is achieved by eliminating the need for a server to explicitly send a challenge as is done by SSH or FIDO when public-key authentication is used. Instead, a passphrase is computed, using a combination of time stamps and public key encryption, and verified by the server. The effect is similar to the use of client certificates, but does not require a certificate authority or some other third party, nor a procedure for obtaining and configuring certificates that most users find too daunting to consider (a program named sbl described below will set up a key pair painlessly and provides buttons to copy data needed by a server to the system clipboard). In addition, client certificates are used when an SSL connection is established, which is problematic for a web site that uses a single TCP socket when only part of the web site should be authenticated.
Secure basic authentication assumes that SSL/TLS will be used for connections between a client and server. As a result,
The passphrase generated in Secure Basic authentication uses
The server stores the user's public key, signature algorithm, and password. To check that a passphrase is valid, the server
In addition to providing some protection against denial of service attacks, The password is useful when certificates use subject alternative names, effectively allowing multiple entities to share a single certificate, and where one may want to be logged into one entity but not another.
Typically a client will reuse a passphrase that it has previously generated until that passphrase fails. It that is done, the client should also check that the corresponding certificate has not been changed: otherwise a MITM attack is possible, although that would require compromising the network infrastructure (routers, DNS servers, etc.)
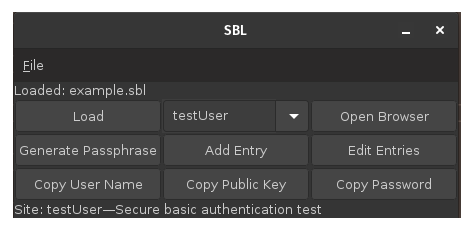
A program, sbl, will generate passphrases and copy them to the clipboard so that they can be pasted into a dialog box provided by a browser that does not support secure basic authentication. The following screenshot shows the user interface:

This program is task-oriented, which is why the graphical user interface is primarily a set of buttons. An unusual feature is that, when it opens a browser, sbl will copy a user name and passphrase to the clipboard in such a way that paste operations alternate between the two. Some operations are also accessible via a menu, which provides keyboard shortcuts for frequently used operations.
Basic authentication defines a "realm" as a name used to define a "protection space" (as defined in RFC 7235, Section 2.2 Secure basic authentication uses a stylized encoding for realms: if a realm sent by a server to a client starts with
The realm is not used when a passphrase is generated for pragmatic reasons: programs such as sbl that generate passphrases may not be able to determine what the realm is (sbl opens an SSL/TLS connection to a server but does not use HTTP or HTTPS, and consequently cannot determine the realm. While the realm could be specified explicitly in an sbl's input file, the realm can be changed by a server at any time, and it is not desirable to burden the user with having to figure out when this has happened (when authenticating, firefox, for example, does not tell users what the realm is).
A server should support the following limits and timeouts
The use of timestamps prevents old passphrases from being reused, even though, with SSL/TLS, it would be very difficult to obtain one.
Implementing secure basic authentication in a browser should be roughly comparable to implementing or modifying a password manager.
The current implementation has two limitations, mostly because of the existing Java APIs:
The program sbl uses GPG to encrypt the private key corresponding to the public key used by a server for authentication, and that private key can be encrypted so that more than one user can decrypt it. For a small web site for which several individuals need access to a role-specific management account, one can simply provide an sbl file on that web site, and a browser can then save that file or simply run it, automatically starting sbl. This can simplify managing the web site as users don't have to set up an account or remember a website-specific password (but will need to install sbl and GPG). GPG key servers can eliminate the need for a user to explicitly provide a GPG key.
This capability may be particularly useful for small websites that support a relatively small number of users and that do not have a full-time staff to manage them. There's one security risk in placing an sbl file on a publicly accessible website: additional users can get access to an encrypted private key, but the mitigating factor is that the key is encrypted using GPG and without access to the GPG private key, breaking GPG encryption is nearly impossible: it would require a brute-force search of 2128 keys.
As a convenience, sbl allows GPG user ID's to be listed with multiple -r options, followed by the configuration-file name. This will cause a new key pair to be generated with a new set of users being able to access the private key.
Public key:
signature-algorithm: SHA256withECDSA -----BEGIN EC PUBLIC KEY----- MFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAE1IC0QbQQPpt4xWzI8IHya5HEOGZu fzjm5LztuExU2T+tvZhXRBQRewShwwoxbPUV+NZo7YHpXXHfMciMLKpzFQ== -----END EC PUBLIC KEY-----
A passphrase using a Google certificate, the user name "foo", the password "foo", and the private key corresponding to the public key shown above is
0JmMZEQapr8wRQIgWsnL7ZPs-zpaEIf77lISXyxvXp6AOAIL9c25BAxV85MCIQCSZ80 GzmAiGyUeRz4qTi_ZY0akLVCRc_ZCwLgheej7yQ==
Similarly, a passphrase using a Yahoo certificate, the user name "foo", the password "foo", and the private key corresponding to the public key shown above is
65mMZOzrwhUwRQIgNFXaAbvgssv68McvgXsy71pkO9_rNAxKfA1Ft5hpEN8CIQC49q9 EZkGuAZaQIpl1efRDE2vEbM8l83CtKl8-mLzWEg==
Neither passphrase includes a line break: the version above splits the passphrases into two lines for readability.
Successfully verifying these passphrases requires that that the public key can verify a signature constructed using the user's password and the server's certificate. Note that two different servers cannot use the same certificate without sharing the certificate's private key. In addition, the signature includes a timestamp, encoded in the passphrase, so that passphrases are valid for only a short time.
For reference, The Google certificate used was
and the Yahoo certificate used was-----BEGIN CERTIFICATE----- MIIEhzCCA2+gAwIBAgIQeE1X6idB65EKlmpjjlYJLTANBgkqhkiG9w0BAQsFADBG MQswCQYDVQQGEwJVUzEiMCAGA1UEChMZR29vZ2xlIFRydXN0IFNlcnZpY2VzIExM QzETMBEGA1UEAxMKR1RTIENBIDFDMzAeFw0yMzA1MjIwODIyNDBaFw0yMzA4MTQw ODIyMzlaMBkxFzAVBgNVBAMTDnd3dy5nb29nbGUuY29tMFkwEwYHKoZIzj0CAQYI KoZIzj0DAQcDQgAEHCWyiOoDrh+v8ZunI5Tzu0tI5iWMnG3vn+RhpBFYKVr4RDVS wzdzNJR+8MpX4O+DzshyDY0UY5bwlcC31B2SDKOCAmcwggJjMA4GA1UdDwEB/wQE AwIHgDATBgNVHSUEDDAKBggrBgEFBQcDATAMBgNVHRMBAf8EAjAAMB0GA1UdDgQW BBQ73ilI6sfX8FuteFkvDISc6KCC0DAfBgNVHSMEGDAWgBSKdH+vhc3ulc09nNDi RhTzcTUdJzBqBggrBgEFBQcBAQReMFwwJwYIKwYBBQUHMAGGG2h0dHA6Ly9vY3Nw LnBraS5nb29nL2d0czFjMzAxBggrBgEFBQcwAoYlaHR0cDovL3BraS5nb29nL3Jl cG8vY2VydHMvZ3RzMWMzLmRlcjAZBgNVHREEEjAQgg53d3cuZ29vZ2xlLmNvbTAh BgNVHSAEGjAYMAgGBmeBDAECATAMBgorBgEEAdZ5AgUDMDwGA1UdHwQ1MDMwMaAv oC2GK2h0dHA6Ly9jcmxzLnBraS5nb29nL2d0czFjMy9RT3ZKME4xc1QyQS5jcmww ggEEBgorBgEEAdZ5AgQCBIH1BIHyAPAAdQCzc3cH4YRQ+GOG1gWp3BEJSnktsWcM C4fc8AMOeTalmgAAAYhCxJw4AAAEAwBGMEQCICQZq3uo6Q7sg2kJps2pegHGTjEX kFILwrlU85efTTJEAiBSLjgX2DbpuYnOgEDbdLwh2TsoeAJV+84K7lC0bBRl2QB3 AK33vvp8/xDIi509nB4+GGq0Zyldz7EMJMqFhjTr3IKKAAABiELEm1kAAAQDAEgw RgIhAJO/dIr2uxOEECYPdb9YZssSfqIBeVtv5jB+Huie9BNUAiEAnlE3tT3Jyxn+ rSt6G8LSw0mksybws40jsNSae2ZwTzUwDQYJKoZIhvcNAQELBQADggEBAJEsPm1N Q+cLrIZ9Bf7IMPfgqxJHWqshRVmnyBTwxG8AnYOYL8pyTtaNsCyFt3vjPwd+T/rI i/64uTG7FCeE48AJ2bL0O8I49CUF3A+JIafRtPziAWRjINBGntK9UqIfZdIvYr9S RbNU9h+sXz1/z1jpUk9D51eJHnil8Y4kSr953E49KkRjMf4Y24uamYohCm3eqkZj 2uG+pDvMhQX0iorPbcRiOSVl8Mt3QLrbQKIerQoW8ymb29tepeFE5g6tU8kSCv20 ndv9dItcEhiAYYpE95mACtbeK+R23VM00zSEKzTLkYINNc1aJ6M9Hm9yu/TXubUg ZqznT7rvz6WIqmw= -----END CERTIFICATE-----
These certificates, of course, are periodically updated. Regardless, a useful exercise for a reader so inclined is to try to create new passphrases that can be verified with either certificate, given the public key and password provided above—a task that would have to break public key encryption in order to succeed.-----BEGIN CERTIFICATE----- MIIHCjCCBfKgAwIBAgIQCOMVxD5bPAxsFkDF4E5b+DANBgkqhkiG9w0BAQsFADBw MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3 d3cuZGlnaWNlcnQuY29tMS8wLQYDVQQDEyZEaWdpQ2VydCBTSEEyIEhpZ2ggQXNz dXJhbmNlIFNlcnZlciBDQTAeFw0yMzA1MDIwMDAwMDBaFw0yMzEwMjUyMzU5NTla MGcxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlhMRIwEAYDVQQHEwlT dW5ueXZhbGUxGzAZBgNVBAoTEk9hdGggSG9sZGluZ3MgSW5jLjESMBAGA1UEAxMJ eWFob28uY29tMFkwEwYHKoZIzj0CAQYIKoZIzj0DAQcDQgAEBXKfj6BfY2g7WbNG aciQoIAf/xFEh8BtJXrJmjG2Bq46d4VdRZkIFQgNC0P1Ku2t9HdjfA1bGreUyjGc TKaOKqOCBHIwggRuMB8GA1UdIwQYMBaAFFFo/5CvAgd1PMzZZWRiohK4WXI7MB0G A1UdDgQWBBSEIFgNJdSMvmV7RNRP+zIIyAnYUzCCATIGA1UdEQSCASkwggElggl5 YWhvby5jb22CD3R3LnJkLnlhaG9vLmNvbYIKcy55aW1nLmNvbYIMbWJwLnlpbWcu Y29tgg9oay5yZC55YWhvby5jb22CFmZyLWNhLnJvZ2Vycy55YWhvby5jb22CEGRk bC5mcC55YWhvby5jb22CE2NhLnJvZ2Vycy55YWhvby5jb22CD2NhLm15LnlhaG9v LmNvbYINYnJiLnlhaG9vLm5ldIIQYWRkLm15LnlhaG9vLmNvbYILKi55YWhvby5j b22CDyoud3d3LnlhaG9vLmNvbYIRKi5tZWRpYS55YWhvby5jb22CGSouZ2xvYmFs LnZlc3BhLm9hdGguY2xvdWSCDyouYXR0LnlhaG9vLmNvbYIOKi5hbXAueWltZy5j b20wDgYDVR0PAQH/BAQDAgeAMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcD AjB1BgNVHR8EbjBsMDSgMqAwhi5odHRwOi8vY3JsMy5kaWdpY2VydC5jb20vc2hh Mi1oYS1zZXJ2ZXItZzYuY3JsMDSgMqAwhi5odHRwOi8vY3JsNC5kaWdpY2VydC5j b20vc2hhMi1oYS1zZXJ2ZXItZzYuY3JsMD4GA1UdIAQ3MDUwMwYGZ4EMAQICMCkw JwYIKwYBBQUHAgEWG2h0dHA6Ly93d3cuZGlnaWNlcnQuY29tL0NQUzCBgwYIKwYB BQUHAQEEdzB1MCQGCCsGAQUFBzABhhhodHRwOi8vb2NzcC5kaWdpY2VydC5jb20w TQYIKwYBBQUHMAKGQWh0dHA6Ly9jYWNlcnRzLmRpZ2ljZXJ0LmNvbS9EaWdpQ2Vy dFNIQTJIaWdoQXNzdXJhbmNlU2VydmVyQ0EuY3J0MAkGA1UdEwQCMAAwggF9Bgor BgEEAdZ5AgQCBIIBbQSCAWkBZwB2AOg+0No+9QY1MudXKLyJa8kD08vREWvs62nh d31tBr1uAAABh9nmwMwAAAQDAEcwRQIgL+HM8l9bk3GKcgy2Dd3zAGHdna0ybQZQ GmsvEwX58TcCIQDYqwMXMRrentSPwuk593MoPnslKVfLqePdwWUHJGRLpwB2ALNz dwfhhFD4Y4bWBancEQlKeS2xZwwLh9zwAw55NqWaAAABh9nmwSYAAAQDAEcwRQIg IhpCW9e04m2ki11BrwWgFi6m8MuFOIccN2+kREJMXP4CIQC2DP911vhghVWIMkdJ 1UPevjgqJsmIyf7ZnovXoHFwLgB1AHoyjFTYty22IOo44FIe6YQWcDIThU070ivB OlejUutSAAABh9nmwMUAAAQDAEYwRAIgBgD7F5RatVyzlFFPbADrBqckIRnZYjDc gIvI1ylO9m0CIFEedXbQft9sszsP/2/Uf0Plx3QhyqVK2xob2rTXspUTMA0GCSqG SIb3DQEBCwUAA4IBAQBNrx7qDppLOKNDj90RlgCUFvPgTvfkEPp6R9XTmXcPE9LP 0r3EZxmik+1/GPZnOAQdC2z9L9/aM8Ir/GLH4igFMyhuJ3X9yiZ5CKX/naObqwNo WrIUy3bMgkn1Mr+C4MDNNjLfOPtX+wsWsWmyzREwvyPXLZlvKtqLA46TOUNY6KgS K8F056eue8ncG4zal1jV6B8PRdBSIH2cWJma4cdNcNY2cMlxiUUlEcJwXNEN+pSq ivTndk4DNACoh0CqVK+fFnkNPlR3t0LefU7oc4bB6iEqqUGvhhmm53MvYGtHXdhS ccR8O2EQZnVa2RKF9NRhQ5QgDa1EJpJlB+VPL7W+ -----END CERTIFICATE-----